Description
In this video I show how to install and use Kalibrate-RTL in Kali Linux, which is useful for finding out the exact frequency for GSM downlinks. (For cheaper software defined radios such as the RTL-SDR, it may in some cases be important to look at the offset, and use the calculated frequency instead of the ARFCN when decoding GSM downlinks. In my case, using either the frequency or ARFCN works.)
If you trust the output from Kalibrate-RTL, you can calculate the exact frequency in the console as follows:
echo $((951400000-23687))
This will output: 951376313 (~951.37MHz)
Topics covered:
– Installation and Basic Usage of Kalibrate-RTL
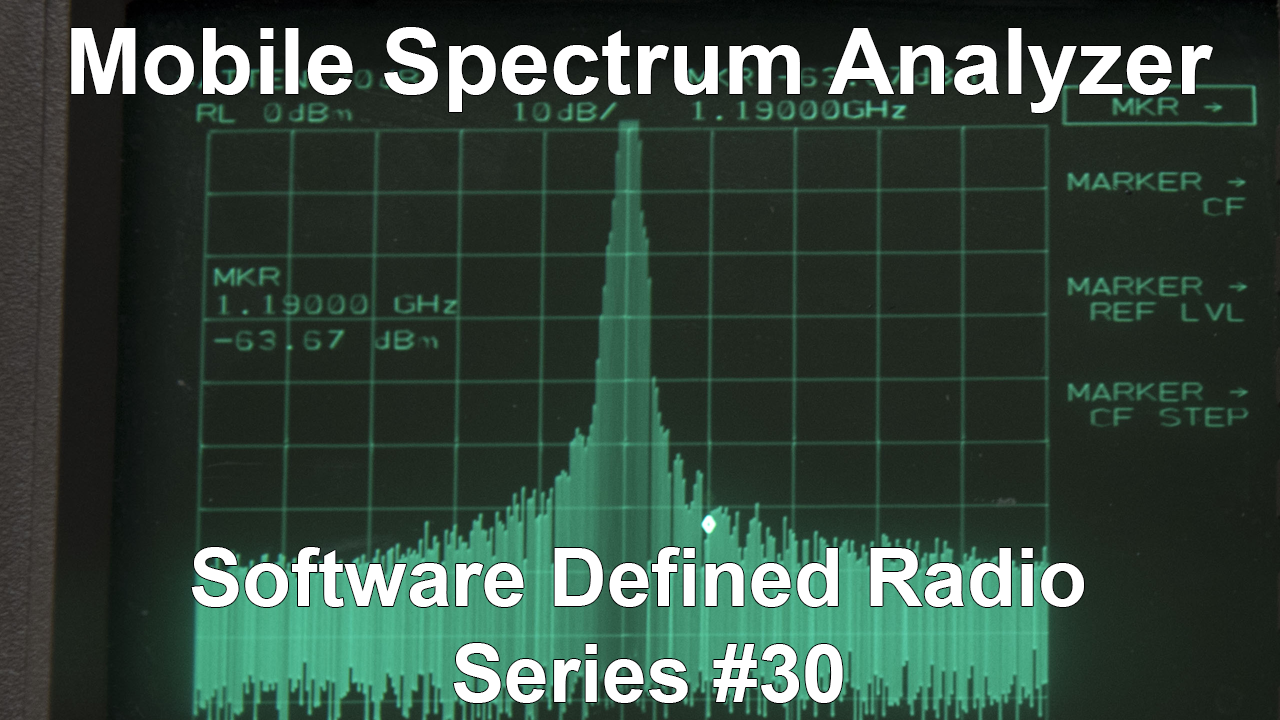
– Confirming Kalibrate-RTL Output in GQRX
Tools:
– kalibrate-rtl
– gqrx
– apt (apt-get & apt-cache)
Stay tuned and subscribe for more upcoming videos showing actual hacks!




Hi Crazy Danish Hacker,
Very interesting articles and most certainly a lot to learn from you.
Our question: We are currently using RTL SDR (Elonics E4000 ) as an IMSI catcher merely for intrusion detection at secure areas in factories, refineries, et al. The challenge is that we can only detect 2G handsets but nothing on 3G or 4G. Any recommendations please?
Thanks, I haven’t done any work on 3G or 4G yet though. But with the “IMSI catcher” program, which is really an “IMSI sniffer” program, I recommend you test the following:
1. Configure a mobile phone to only use 3G or 4G;
2. When it’s quiet at the factory, for example at night I presume, move the mobile phone to within range of the local cell tower;
3. This should trigger a “location update request” packet, I can’t remember the exact name, but this is one of the packets that the “IMSI sniffer” program may look for; and
4. Confirm with e.g. GR-GSM and Wireshark, if a packet containing the mobile phone’s TMSI (or even IMSI) was sent over the 2G network.
This assumes that the telco in your area, is operating both 2G, 3G and 4G towers, so that mobile devices won’t need to do the full switch to another provider’s network when 2G is used.
To make it easier for yourself, extract the TMSI and IMSI before and after you move the mobile phone, within range of the local cell tower. That way you can search for it in Wireshark, instead of looking for a needle in a haystack, because you may have to capture for several minutes.
This advice is mostly based on an idea and an assumption, that the telco’s 2G, 3G and 4G networks are functioning as essentially “one network”, where each have their own strengths and weaknesses. It also assumes, that if a device is connected to the 3G network, then for example “paging requests” may be sent over 2G. I haven’t tested this idea yet myself, but it’s worth trying out as I’m not familiar with 3G and 4G yet. I don’t do a lot of GSM research or testing these days, but on occasion I do try a few things out of interest.
I’m also not familiar with the entire GSM protocol and how it’s designed, as it’s not exactly simple, so my idea above might work, and it may not work. (I do web application security, i.e. hacking websites legally and professionally for a living. Software Defined Radio is just a hobby of mine.)
Note: Depending on your location and the placement of cell towers, the range could be anything from 1km and up to 20km. In my case there’s usually a cell tower within 1-2km, so if you move 5-6km away from the site, then you should be able to conduct this test properly. There are a few open source projects that map the approximate location of cell towers, that you can use to identify where cell towers are located in your area. Sample reference for USA:
https://www.cellmapper.net/map?MCC=310&MNC=120&type=LTE&latitude=38.14645250503634&longitude=-104.29839446201925&zoom=5&showTowers=true&clusterEnabled=true&tilesEnabled=true&heatMapEnabled=false&showOrphans=false&showNoFrequencyOnly=false&showFrequencyOnly=false&showBandwidthOnly=false&DateFilterType=Last&showHex=false&showVerifiedOnly=false&showUnverifiedOnly=false&showLTECAOnly=false&showBand=0&mapType=custom_map&showSectorColours=true
Sample GSMTAP Packet Reference:
https://github.com/Oros42/IMSI-catcher/blob/master/simple_IMSI-catcher.py#L441