Description
In this video I demonstrate how to conduct an automated password guessing attack, against the (Damn Vulnerable Web Application) login screen at the “impossible” level. This is done by using a transparent intercepting proxy (Burp Suite), more specifically the Repeater and Intruder modules.
Other attacks such as session token analysis using the Burp Sequencer module, and basic “old school” SQL injections for login bypasses were also briefly covered.
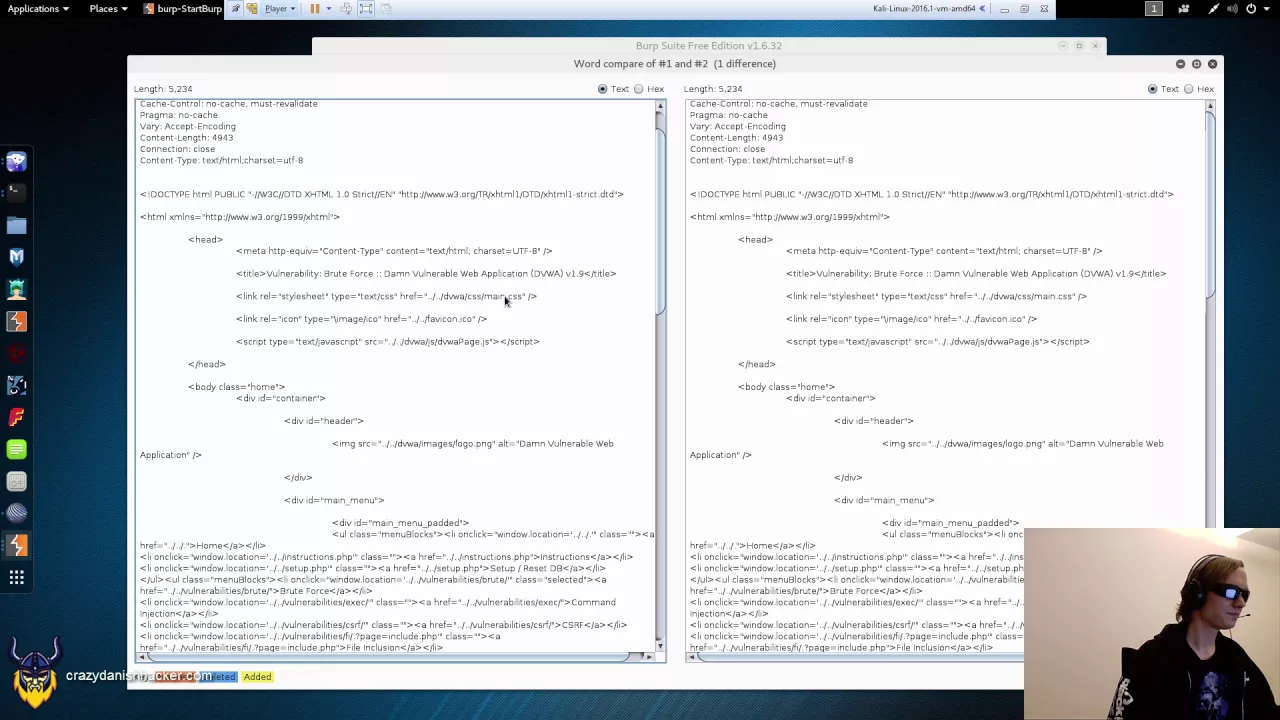
During the password guessing attack, an Anti-CSRF (Cross-Site Request Forgery) token was making it a lot harder for me to conduct the attack, as every single request needed a valid CSRF token. To add on top of that, the “Grep Extract” option within Intruder was not compatible with the DVWA application, as it returns a 302 redirect, instead of a 200 OK response.
This meant that I had to search for alternatives, where a Burp plugin known as CSurfer was identified as working for my purpose, albeit being very slow. In the end everything worked out and I managed to brute-force the (known) password.
Topics covered:
– “Brute-forcing”/Automated password guessing
— Burp Repeater
— Burp Intruder (Advanced level)
– Burp Sequencer (Basic level)
– Burp Proxy (Incl. configuration)
– Basic SQL Injections for Login Bypasses
– Bypassing CSRF Tokens with Burp [Intruder and Repeater]
Burp Suite: https://portswigger.net/burp/
Stay tuned and subscribe for more upcoming videos showing actual hacks!


Recent Comments